Moving Forward Together
In looking at where we are going, there is no way we can not look at where we came from. We came from a group of people who were strong, determined and full of hope. They saw a future through drought, hail and dust storms, and continued to believe that there would be rain.
More times than not, they were not disappointed. The rain came, the crops grew and there was strength in the survival. Since it’s founding in 1919, The Garden City Co-op, Inc. has also hoped for the rain, and when it came, celebrated with its member owners, now over 2,000 strong.
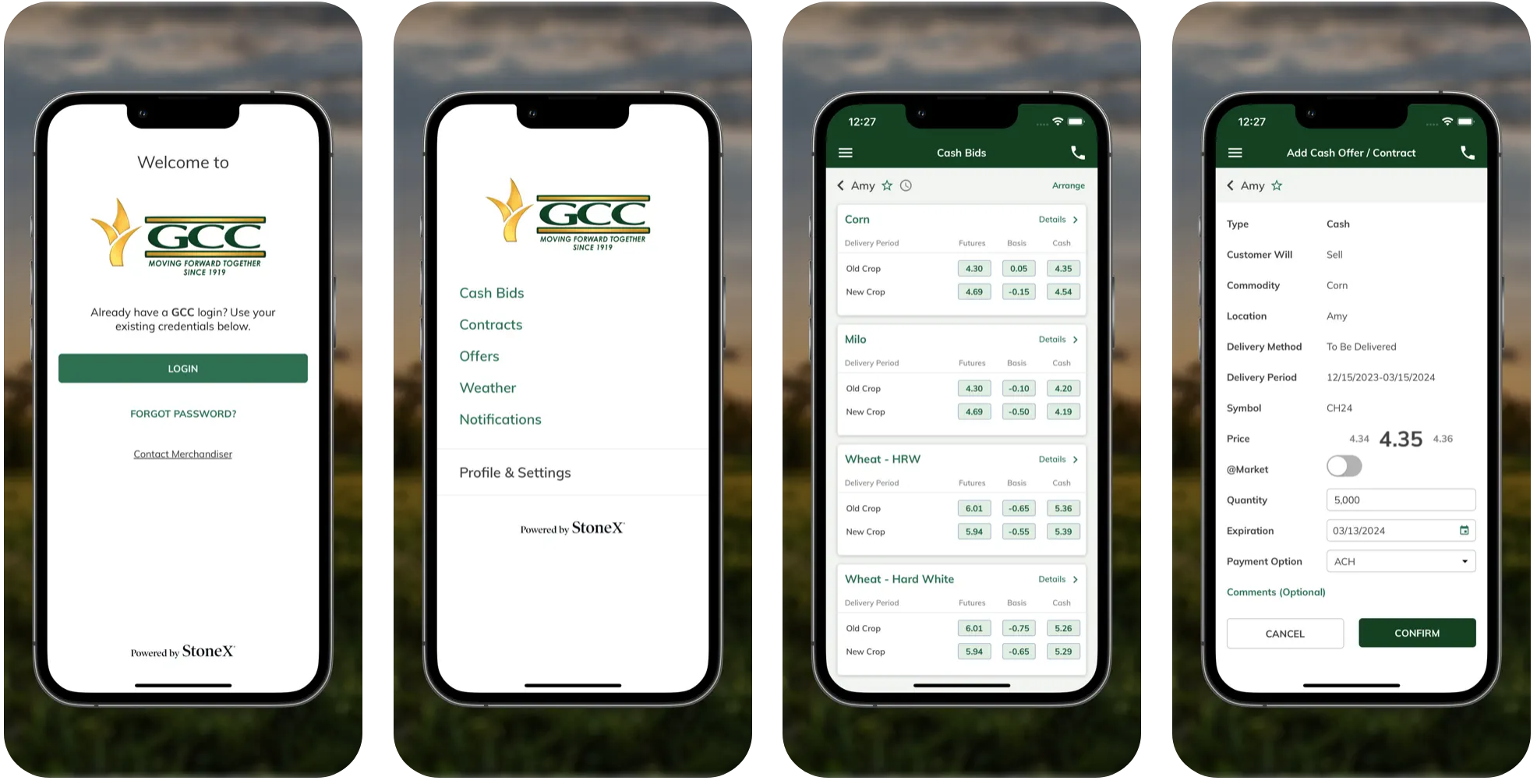
Upgrade to the New GCC Mobile App
Agronomy Insights and Sustainability Initiative Opportunity
Breakthrough AI Technology Leads to the World's First Self-Aware Wheat Stalk
CURRENT GRAIN CASH BIDS
Daily Grain Commentary
Read our daily grain commentary from Stone X
Daily Energy Commentary
Read our daily energy commentary from CHS
U.S. GRAIN MARKET COMMENTARY
GCC WEEKLY MARKET COMMENTARY
GCC E-MAIL NEWSLETTER
Stay up to date with our newsletter.

AG TECH
Our department specializes in Agricultural Technology - handling everything Precision Ag related, as well as Decision Ag, and Internet of Things (IoT).
We follow Ag trends, ensuring we keep our farmer members as well as our neighboring cooperatives up to date in the ever-evolving changes in technology as a participating FieldReveal dealer and mapping center.